The BBC is reporting
that the American Registry for Internet Numbers (ARIN) ran out of spare
IP addresses yesterday. "Companies in North America should now
accelerate their move to the latest version of the net's addressing
system. Now Africa is the only region with any significant blocks of
the older version 4 internet addresses available." A British networking
company that supplies schools has done an analysis on how concerned IT managers should be. This comes almost exactly 3 years after Europe ran out.
Sunday, September 27, 2015
Breaking the Grid Authentication for NEFT transaction ICICI
As I stated in my previous post I was facing a grief with the grid authentication for the completion of a NEFT transaction. Later after a R&D with the entire web and apps of the ICICI found a workaround to bypass this system for a successful money transfer without any silos.
Its been almost 2 days I posted the trouble faced due to this grid system associated.@ICICI care team reached me out in twitter and DM me that the concern team will call me and still waiting for their call.
Firstly I would not be a naysayer for the security system implemented. I do know how much security matters as I germinated from a security domain. I am more skeptical towards the info shared by every executive they defy with ( the only answer was we are deeply sorry for the inconvenience caused you could not proceed the transaction without a grid authentication).
There is a contrary in the workflow :
The major flaw is in when a user initiates a transaction the system couldn't update the users debit card details in real time if the user is not associated to any debit card the system should analyze and authenticate by the alternative means to complete the transaction.
This should happen else leave the end user wait till they receive the debit card for important transactions.
Workaround for this which I used:
When I explored the web login there was no way allowed to complete the transaction , suddenly a spark came into my mind that we are in "apps world" why cant we try the existing apps in my gadget.
Tried would there be a way in imobile and failed miserable , but the tenacity gave me the last trump card app that was pockets . The pockets app acts like a personal wallet where I can add funds from my ICICI account. New user can create a new account (non ICICI user) Existing user can login using the net banking credentials. Once done the way is out add the funds to wallet and now access the registered user with the account from the app and complete your transfer via NEFT with OTP.
MORAL / CONCLUSION: The financial institution who we rely on should educate the customers about the process that's secondary before that the employees inside the bank should know the process and the possibilities to overcome the issues caused.
Do they conduct regular meetings and update whats new they launch what all procedures gets changed and stay update ??
Waiting for a response from #ICICI Hope things will change.
Its been almost 2 days I posted the trouble faced due to this grid system associated.@ICICI care team reached me out in twitter and DM me that the concern team will call me and still waiting for their call.
Firstly I would not be a naysayer for the security system implemented. I do know how much security matters as I germinated from a security domain. I am more skeptical towards the info shared by every executive they defy with ( the only answer was we are deeply sorry for the inconvenience caused you could not proceed the transaction without a grid authentication).
There is a contrary in the workflow :
The major flaw is in when a user initiates a transaction the system couldn't update the users debit card details in real time if the user is not associated to any debit card the system should analyze and authenticate by the alternative means to complete the transaction.
This should happen else leave the end user wait till they receive the debit card for important transactions.
Workaround for this which I used:
When I explored the web login there was no way allowed to complete the transaction , suddenly a spark came into my mind that we are in "apps world" why cant we try the existing apps in my gadget.
Tried would there be a way in imobile and failed miserable , but the tenacity gave me the last trump card app that was pockets . The pockets app acts like a personal wallet where I can add funds from my ICICI account. New user can create a new account (non ICICI user) Existing user can login using the net banking credentials. Once done the way is out add the funds to wallet and now access the registered user with the account from the app and complete your transfer via NEFT with OTP.
MORAL / CONCLUSION: The financial institution who we rely on should educate the customers about the process that's secondary before that the employees inside the bank should know the process and the possibilities to overcome the issues caused.
Do they conduct regular meetings and update whats new they launch what all procedures gets changed and stay update ??
Waiting for a response from #ICICI Hope things will change.
Thursday, September 24, 2015
Silos of Grid security authentication ICICI Bank
Today I am a very disappointed 6-yr customer with ICICI Bank ICICI Bank - Security systems ! Since last night I was trying to make a online transaction to another account and The transaction could not be completed due to the unavailability of the debit card grid value. Day by day technologies grow We use Net banking Mobile banking etc. Even ICICI proudly says cardless cash withdrawals.
Since my debit card has become too old and damaged I have applied for a new one and its under process. Meanwhile if I wish to do a online transaction the ICICI Bank states that
I could not proceed because grid authentication is mandate. Its good that they have implemented a extra layer of security but that security system should not be a grief to customers transaction.This would not be a better option in a longer run. When a customer applied a new card they are unlinking the old card from the account so they can enable the other security options like OTP as an alternate and by not mandating both are required. I hope even the Head of the ICICI would not prefer to use their banking facilities if they face this kind of issues. In a crucial situations to pay your bills the customer care executives are responding that without a grid value we cant help you to proceed is really frustrating they are not not thinking in the lines of a customer or go an extra mile to check what best can be done. When they link the customer's mobile number they can make that as primary and the grid option as secondary if customer further opts during transactions. What are the plan B options if a disaster occurs ??
The customer should be helpless till he receives a new card again. If they comply to various regulatory laws I'm sure they will be aware what BO states.
The grid authentication was first introduced to avoid cyber crooks in credit card transactions. This may work for credit cards but linking this to internet banking and debit card will be a failing factor. However there should be certain measures to be taken by ICICI to provide a Plan B for continuing the services without interruption by authenticating them by other security parameters.
Since my debit card has become too old and damaged I have applied for a new one and its under process. Meanwhile if I wish to do a online transaction the ICICI Bank states that
I could not proceed because grid authentication is mandate. Its good that they have implemented a extra layer of security but that security system should not be a grief to customers transaction.This would not be a better option in a longer run. When a customer applied a new card they are unlinking the old card from the account so they can enable the other security options like OTP as an alternate and by not mandating both are required. I hope even the Head of the ICICI would not prefer to use their banking facilities if they face this kind of issues. In a crucial situations to pay your bills the customer care executives are responding that without a grid value we cant help you to proceed is really frustrating they are not not thinking in the lines of a customer or go an extra mile to check what best can be done. When they link the customer's mobile number they can make that as primary and the grid option as secondary if customer further opts during transactions. What are the plan B options if a disaster occurs ??
The customer should be helpless till he receives a new card again. If they comply to various regulatory laws I'm sure they will be aware what BO states.
The grid authentication was first introduced to avoid cyber crooks in credit card transactions. This may work for credit cards but linking this to internet banking and debit card will be a failing factor. However there should be certain measures to be taken by ICICI to provide a Plan B for continuing the services without interruption by authenticating them by other security parameters.
Saturday, September 19, 2015
Homegrown linux distro by M$
Microsoft has built a Linux distro, and is using it for their Azure data centers.
From their blog post: "It is a cross-platform modular operating system
for data center networking built on Linux." Apparently, the existing SDN
(Software Defined Network) implementations didn't fit Microsoft's plans
for the ACS (Azure Cloud Switch), so they decided to roll their own
infrastructure. No explanation why they settled on Linux.

Its own Linux-based operating system called Azure Cloud Switch (ACS) and believe me, under Satya Nadella, Microsoft has become more open than ever.

Its own Linux-based operating system called Azure Cloud Switch (ACS) and believe me, under Satya Nadella, Microsoft has become more open than ever.
The
Purpose of developing Linux-based Azure Cloud Switch (ACS) operating system at
Microsoft is to make it simpler to control the hardware from multiple
vendors (such as Switches) that powers their cloud-based services.
However, Microsoft's Linux
distribution is not going to appear on Desktops or Servers anytime soon,
because this isn't a typical consumer-grade Operating System.
For Now, Azure Cloud Switch
(ACS) Linux OS is just an internal tool that Microsoft uses to "debug,
fix as well as test software bugs much faster", scale down software
and develop features for enterprise and cloud computing services.
Microsoft Azure Cloud Switch (ACS) was demonstrated at the SIGCOMM conference in August 2015 at Imperial College London.
Microsoft Azure Cloud Switch (ACS) was demonstrated at the SIGCOMM conference in August 2015 at Imperial College London.
Saturday, September 12, 2015
BitTorrent based DOS DNS- attacks proved
New research from City University London has demonstrated the
practicability of using highly popular file-sharing clients based on the
BitTorrent protocol to accomplish Denial of Service (DOS) attacks that
are orders of magnitude more aggressive and powerful than conventional
techniques currently in use.
The paper [PDF], entitled P2P File-Sharing in Hell: Exploiting BitTorrent Vulnerabilities to Launch Distributed Reflective DoS Attacks, details the efforts of researcher Florian Adamsky (along with fellows Syed Ali Khayam of Santa Clara-based security outfit PLUMgrid
and Rudolf Jäger of The Mittelhessen University of Applied Sciences in
Germany) to prove that attackers can exploit vulnerabilities in
BitTorrent clients in order to effect Distributed Reflective Denial of
Service (DRDoS) attacks.
The paper states “Our protocol analysis shows that BitTorrent is highly vulnerable to DRDoS attacks. An attacker is able to amplify the traffic beginning from 4–54.3 times.”
DRDoS attacks rely on the misconfiguration of Domain Name System (DNS) servers to help attackers spoof the apparent originating source of a ‘request flood’ – the type of information overload that can bring down a website or organizational infrastructure for days, or weeks.
A DRDoS attack routes the aggressive traffic through ‘amplifiers’, and these reflect the traffic to the victim. In the case of a BitTorrent-based attack the protocols exploited are Distributed Hash Table (DHT), Micro Transport Protocol (uTP), BitTorrent Sync (BTSync) and Message Stream Encryption (MSE). “Since these protocols do not include mechanisms to prevent IP source address spoofing,” the paper explains “an attacker can use peer-discovery techniques like trackers, DHT or Peer Exchange (PEX) to collect millions of possible amplifiers.”
Apparently the BitTorrent clients that are most susceptible to the attack are also those that are most widely-used; the report observes that ‘the most widely-used BitTorrent clients like uTorrent, Mainline and Vuze are also the most vulnerable ones.” Three years ago the number of users of uTorrent alone was estimated at 150 million, making the potential devastation of Torrent-based DOS attack a formidable one.
In terms of security for the attacking actor, this attack method has the advantage of being undetectable by standard firewalls due to the encrypted nature of the protocol, and would require deep packet inspection to identify. Additionally a BitTorrent-based DRDoS attack has the advantage of being launchable from a single computer. The potency of this attack format is further reinforced by the multiple connections that BitTorrent is able to leverage; clients operate separate connection threads on multiple ports, which can result in a client dominating available bandwidth.
BitTorrent has since responded to the Adamsky paper. In a blog post today the company outlines how its engineering teams have been working to mitigate the possibility of DrDoS attacks. To find out more see here.
The paper states “Our protocol analysis shows that BitTorrent is highly vulnerable to DRDoS attacks. An attacker is able to amplify the traffic beginning from 4–54.3 times.”
DRDoS attacks rely on the misconfiguration of Domain Name System (DNS) servers to help attackers spoof the apparent originating source of a ‘request flood’ – the type of information overload that can bring down a website or organizational infrastructure for days, or weeks.
A DRDoS attack routes the aggressive traffic through ‘amplifiers’, and these reflect the traffic to the victim. In the case of a BitTorrent-based attack the protocols exploited are Distributed Hash Table (DHT), Micro Transport Protocol (uTP), BitTorrent Sync (BTSync) and Message Stream Encryption (MSE). “Since these protocols do not include mechanisms to prevent IP source address spoofing,” the paper explains “an attacker can use peer-discovery techniques like trackers, DHT or Peer Exchange (PEX) to collect millions of possible amplifiers.”
Apparently the BitTorrent clients that are most susceptible to the attack are also those that are most widely-used; the report observes that ‘the most widely-used BitTorrent clients like uTorrent, Mainline and Vuze are also the most vulnerable ones.” Three years ago the number of users of uTorrent alone was estimated at 150 million, making the potential devastation of Torrent-based DOS attack a formidable one.
In terms of security for the attacking actor, this attack method has the advantage of being undetectable by standard firewalls due to the encrypted nature of the protocol, and would require deep packet inspection to identify. Additionally a BitTorrent-based DRDoS attack has the advantage of being launchable from a single computer. The potency of this attack format is further reinforced by the multiple connections that BitTorrent is able to leverage; clients operate separate connection threads on multiple ports, which can result in a client dominating available bandwidth.
BitTorrent has since responded to the Adamsky paper. In a blog post today the company outlines how its engineering teams have been working to mitigate the possibility of DrDoS attacks. To find out more see here.
Friday, September 11, 2015
Fireye tries to stifle its vulnerabilities in its suite from public disclosure
Felix Wilhelm, a security researcher for ERNW GmBH,
made FireEye aware of the vulnerabilities five months ago, and
reportedly worked with the company to help them resolve the issues
successfully. But FireEye eventually decided that no disclosure of the
vulnerabilities should be allowed to take place.
FireEye, founded in 2004, is a leading network security company focused on protecting businesses from malware, zero-day exploits and other cyber attacks. The U.S.-based firm has over 2,500 customers globally, including Fortune 500 companies and many federal departments. FireEye was tightly involved in cyber investigations following the high-profile attacks on Sony Pictures and Anthem.
Leading network security company FireEye, which has customers in government and the Fortune 500 list, has caused a controversy at a London security conference today after its legal attempts to stop a keynote speech detailing the repair of major security loopholes in its customer-facing systems this year. Reported among these now-fixed vulnerabilities were the running of a significant number of FireEye's Apache-based security servers as 'root' — meaning that any attacker able to compromise the servers would have had absolute power over all its operations and commercial connections.
FireEye, founded in 2004, is a leading network security company focused on protecting businesses from malware, zero-day exploits and other cyber attacks. The U.S.-based firm has over 2,500 customers globally, including Fortune 500 companies and many federal departments. FireEye was tightly involved in cyber investigations following the high-profile attacks on Sony Pictures and Anthem.
Leading network security company FireEye, which has customers in government and the Fortune 500 list, has caused a controversy at a London security conference today after its legal attempts to stop a keynote speech detailing the repair of major security loopholes in its customer-facing systems this year. Reported among these now-fixed vulnerabilities were the running of a significant number of FireEye's Apache-based security servers as 'root' — meaning that any attacker able to compromise the servers would have had absolute power over all its operations and commercial connections.
Wednesday, September 9, 2015
Count on Google to not only deliver search results
Google is preparing to launch a produce and grocery delivery service in two cities, one of them San Francisco. The service will be powered by Google Express, which already delivers
dry foods and other merchandise to customers, and it will partner with
Whole Foods and Costco. It’ll compete with FreshDirect and Amazon Fresh. While the e commerce war has started long back and its not surprising that google is trying to test this space. Online grocery shopping is a nearly $11 billion business in the U.S., with 9.6% annual expected growth. Interestingly, both groceries and restaurant delivery (called food tech
in Indian venture capital lingo) are crowded and popular businesses in
India, with a clutch of start-ups competing for business.
Google is investing in delivery services for homes and businesses as it seeks to attract more traffic to its websites. The move puts the company in more direct competition with Amazon, which has rolled out its AmazonFresh service in several US cities.
Google is investing in delivery services for homes and businesses as it seeks to attract more traffic to its websites. The move puts the company in more direct competition with Amazon, which has rolled out its AmazonFresh service in several US cities.
Monday, September 7, 2015
Solving a educational problem
This project lead by facebook and its being developed using Ruby On Rails. Gushing in July that Facebook engineers had solved one of education's biggest problems, Melinda Gates perhaps set up Segway-like expectations for Facebook's education software. And while The Verge sings the praises of what appears to be progress-tracking dashboards that connect students to mostly free 3rd-party lessons — not unlike Khan Academy or even the 50-year-old PLATO system — it's hard to get jazzed based on the screenshots (1, 2, 3) that Facebook provided in a .zip file accompanying its announcement. The "personalized learning plan" dashboards are a joint effort of Facebook and the Meg Whitman-led and backed
Summit charter schools. In a nice
circle-of-tech-CEO-education-reform-life twist, the first Summit high
school opened in a building in Redwood City after students attending the
Bill Gates-touted and backed Silicon Valley High Tech High charter
there were evicted to make way, and the Gates Foundation is now spending $8M
to bring HP CEO Whitman's Summit charter schools — and presumably
Facebook CEO Mark Zuckerberg's personalized learning plans — to Seattle
children.
Sunday, September 6, 2015
Answer to the question why kattapa killed baahubali
why Kattappa killed Baahubali ??
The answer would be simple if we have watched every scenes very keen ;)
As SS Rajamouli stated even to have a small idea of where the answer to the question might be, we should look at the climax of Papanasam or Drishyam
So there lies a hint that to save his daughter he get off scot-free
In this case Devasena would be kattappa's daughter
In a scene to afford kattapa's food Baahubali calls him as mama.
In the climax Baahubali's son calls kattapa as his grandfather so the answer to the question is solved.
The answer would be simple if we have watched every scenes very keen ;)
As SS Rajamouli stated even to have a small idea of where the answer to the question might be, we should look at the climax of Papanasam or Drishyam
So there lies a hint that to save his daughter he get off scot-free
In this case Devasena would be kattappa's daughter
In a scene to afford kattapa's food Baahubali calls him as mama.
In the climax Baahubali's son calls kattapa as his grandfather so the answer to the question is solved.
Saturday, September 5, 2015
Docstoc isn’t the only product on Intuit’s chopping block
Today morning I received a email stating that Service Discontinuation Notice for its members. It was one of the good electronic document sharing service similar to slide share and rest others. Since Intuit is into accounting and taxation products the new decision would be to sharpen its focus on building ecosystems for taxation and small businesses. Docstoc appears to be another victim of Intuit’s new execution plan. "No pun intended".
Docstoc was founded eight-and-a-half years ago in Santa Monica, Ca. The company raised just $4 million across two funding rounds, including from Crosscut Ventures and Rustic Canyon Ventures.
Later after acquisition Docstoc cofounder and CEO Jason Nazar told that it took seven years to build this. However, the team said it plans to continue to support existing "premium" customers, but won’t allow new registrations.
Docstoc was founded eight-and-a-half years ago in Santa Monica, Ca. The company raised just $4 million across two funding rounds, including from Crosscut Ventures and Rustic Canyon Ventures.
Later after acquisition Docstoc cofounder and CEO Jason Nazar told that it took seven years to build this. However, the team said it plans to continue to support existing "premium" customers, but won’t allow new registrations.
Friday, September 4, 2015
Alcohol Still Being Legal
There’s a very common drug-policy talking point that’s meant to convey the absurdity of the war on drugs: alcohol is more dangerous than marijuana, even though alcohol is legal and marijuana is not.
Perhaps the biggest supporting evidence for this point is a 2010 study published in The Lancet that ranked alcohol as the most dangerous drug in the United Kingdom, surpassing heroin, crack cocaine, and marijuana. That study has drawn widespread media attention from entities like Vox, etc.
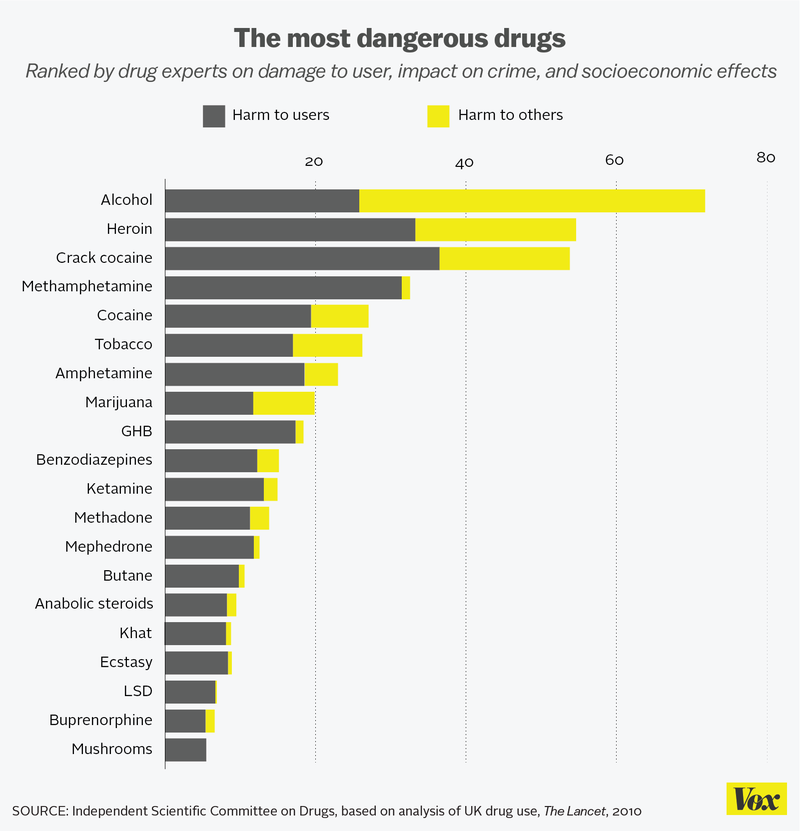
Experts say alcohol scored so high because it is so widely used and has devastating consequences not only for drinkers but for those around them. “Just think about what happens (with alcohol) at every football game,” said Wim van den Brink, a professor of psychiatry and addiction at the University of Amsterdam. He was not linked to the study and co-authored a commentary in the Lancet. When drunk in excess, alcohol damages nearly all organ systems. It is also connected to higher death rates and is involved in a greater percentage of crime than most other drugs, including heroin, writes Maria Cheng of NBC News.
But still here are 5 ways in which alcohol is aiding in increased profits for certain players
According to an assessment recently published in the British Columbia Mental Health and Addictions Journal, health-related costs for alcohol consumers are eight times greater than those for cannabis consumers. This leads to more medication, therapy and medical expenses which the health system profits generously from.
The official publication of the Scientific Research Society, American Scientist, reported that alcohol is one of the most toxic drugs and using just 10 times what one would use to get the desired effect could lead to death. According to the CDC, hundreds of alcohol overdose deaths occur in the United States each year. Again this leads to increased revenues and funding at the expense of lives.
Researchers from the Boston University School of Medicine (BUSM) and Boston University School of Public Health (BUSPH) have shown that alcohol is a major contributor to cancer and drinking even small amounts of alcohol, as little as one drink, can increase the risk of developing cancer. Alcohol, regardless of its type (i.e. beer, wine, liquor, etc) is a class A1 carcinogen which are confirmed human carcinogens. Alcohol consumption has been causally related with breast cancer for some time. Increasing evidence indicates a stronger association with neoplasms, though the risk is elevated for other types of breast cancers too. Alcohol is associated with at least 7 different types of cancers.
Since public of opinion of alcohol is not as critical as that of other addictive substances, its addiction becomes very easy. Alcohol is proven to worsen other addictive tendencies such as gambling, smoking, overeating, other drugs and many other physical and psychological dependencies which drive economies worldwide. Research published in the journal Alcoholism: Clinical & Experimental Research, found that 36 percent of hospitalized assaults and 21 percent of all injuries are attributable to alcohol use by the injured person which alone increases overall revenue of hospitals, clinics and several different health professionals.
Domestic violence and sexual assault are quite often caused by alcohol abuse. A study conducted by the Research Institute on Addictions found that among individuals who were chronic partner abusers, the use of alcohol was associated with significant increases in the daily likelihood of male-to-female physical aggression. Specifically, the odds of abuse were eight times higher on days when men were drinking; the odds of severe abuse were 11 times higher. According to the Rape, Abuse and Incest National Network (RAINN) website highlights alcohol as the “most commonly used chemical in crimes of sexual assault” and provides information on an array of other drugs that have been linked to sexual violence. This one drug alone is estimated for at least 12% of all incarcerations. And America’s obsession with prison and its business is well known to everyone.
Perhaps the biggest supporting evidence for this point is a 2010 study published in The Lancet that ranked alcohol as the most dangerous drug in the United Kingdom, surpassing heroin, crack cocaine, and marijuana. That study has drawn widespread media attention from entities like Vox, etc.

Experts say alcohol scored so high because it is so widely used and has devastating consequences not only for drinkers but for those around them. “Just think about what happens (with alcohol) at every football game,” said Wim van den Brink, a professor of psychiatry and addiction at the University of Amsterdam. He was not linked to the study and co-authored a commentary in the Lancet. When drunk in excess, alcohol damages nearly all organ systems. It is also connected to higher death rates and is involved in a greater percentage of crime than most other drugs, including heroin, writes Maria Cheng of NBC News.
But still here are 5 ways in which alcohol is aiding in increased profits for certain players
- Higher health related costs:
According to an assessment recently published in the British Columbia Mental Health and Addictions Journal, health-related costs for alcohol consumers are eight times greater than those for cannabis consumers. This leads to more medication, therapy and medical expenses which the health system profits generously from.
- The business of death
The official publication of the Scientific Research Society, American Scientist, reported that alcohol is one of the most toxic drugs and using just 10 times what one would use to get the desired effect could lead to death. According to the CDC, hundreds of alcohol overdose deaths occur in the United States each year. Again this leads to increased revenues and funding at the expense of lives.
- Cancer hospitals are in demand
Researchers from the Boston University School of Medicine (BUSM) and Boston University School of Public Health (BUSPH) have shown that alcohol is a major contributor to cancer and drinking even small amounts of alcohol, as little as one drink, can increase the risk of developing cancer. Alcohol, regardless of its type (i.e. beer, wine, liquor, etc) is a class A1 carcinogen which are confirmed human carcinogens. Alcohol consumption has been causally related with breast cancer for some time. Increasing evidence indicates a stronger association with neoplasms, though the risk is elevated for other types of breast cancers too. Alcohol is associated with at least 7 different types of cancers.
- Alcohol is propelling economies?
Since public of opinion of alcohol is not as critical as that of other addictive substances, its addiction becomes very easy. Alcohol is proven to worsen other addictive tendencies such as gambling, smoking, overeating, other drugs and many other physical and psychological dependencies which drive economies worldwide. Research published in the journal Alcoholism: Clinical & Experimental Research, found that 36 percent of hospitalized assaults and 21 percent of all injuries are attributable to alcohol use by the injured person which alone increases overall revenue of hospitals, clinics and several different health professionals.
- Prison industrial complex
Domestic violence and sexual assault are quite often caused by alcohol abuse. A study conducted by the Research Institute on Addictions found that among individuals who were chronic partner abusers, the use of alcohol was associated with significant increases in the daily likelihood of male-to-female physical aggression. Specifically, the odds of abuse were eight times higher on days when men were drinking; the odds of severe abuse were 11 times higher. According to the Rape, Abuse and Incest National Network (RAINN) website highlights alcohol as the “most commonly used chemical in crimes of sexual assault” and provides information on an array of other drugs that have been linked to sexual violence. This one drug alone is estimated for at least 12% of all incarcerations. And America’s obsession with prison and its business is well known to everyone.
Tuesday, September 1, 2015
Linux Kernal 4.2 Released
The Linux 4.2 kernel is now available. This kernel is one of the biggest kernel releases in recent times
and introduces rewrites of some of the kernel's Intel Assembly x86
code, new ARM board support, Jitter RNG improvements, queue spinlocks,
the new AMDGPU kernel driver, NCQ TRIM handling, F2FS per-file
encryption, and many other changes to benefit most Linux users.
Subscribe to:
Posts (Atom)

