On April 21,an anonymous hacker used Weblogic and Websphere deserialization vulnerability to deliver Greystars ransomware to 100 enterprise servers. It encrypted important files in the server and demanded 0.08 bitcoins. The ransom is currently about RMB 4,761. "No file" attack.
The Greystars ransomware virus draws on the "fileless" attack that has become very popular in recent years. All work is done in the Windows legitimate process Powershell - hackers exploit Weblogic deserialization exploits to attack the server and control the server to download the first stage payload hosted on Gist. And run, the load reads the image hosted on Gist with embedded malicious content, decrypts the content of the image and obtains the second stage load and finally executes it in the PowerShell process. Figure 1 shows the complete attack flow.
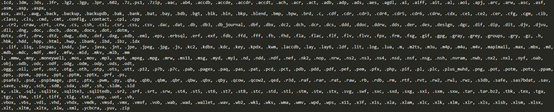
Greystars ransomware encrypt computer with 422 kinds of file formats, including not only common documents, pictures, database files, but also includes some of the script files required for the server to run, including python scripts, PHP scripts, PowerShell scripts. During the encryption process, the Greystars ransomware virus will avoid other directories except the desktop folder and the document folder in the C drive to ensure the normal operation of the system and end the database-related processes to ensure that the database file is successfully encrypted. Because the Greystars ransomware uses the method of “encrypting the original file à generating a new file ànd deleting the original file”, some directories with only read-only privileges will appear to have the encrypted files that do not exist but the original files are deleted. This results in some The server could not recover the file by paying the ransom. Figure 5 shows the file format encrypted by the Greystars ransomware virus.
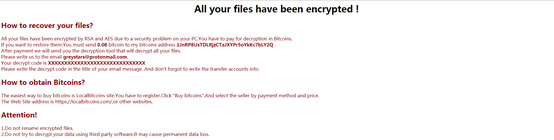
All encrypted files will be suffixed with "greystars@protonmail.com". The generated ransom information requires the victim to transfer a ransom of 0.08 bitcoins to the specified address to decrypt the file. Figure 6 shows ransom information.
Import the rules that are listed below.
Block executable in %AppData%:
The Greystars ransomware virus draws on the "fileless" attack that has become very popular in recent years. All work is done in the Windows legitimate process Powershell - hackers exploit Weblogic deserialization exploits to attack the server and control the server to download the first stage payload hosted on Gist. And run, the load reads the image hosted on Gist with embedded malicious content, decrypts the content of the image and obtains the second stage load and finally executes it in the PowerShell process. Figure 1 shows the complete attack flow.
Figure 1 The complete attack process of Greystars ransomware
The first stage attack payload hosting address is
hxxps://raw.githubusercontent.com/Tree1985/metasploit-framework/master/metasploit.
The hackers successfully use Weblogic deserialization vulnerability to invade the server and execute the command shown in FIG. 2 to download the attack payload from the hosted address. Unlike most hackers who use personal domain names as payload download addresses, Greystars ransomware chose Gist to host the load. The advantage of this is that raw.githubusercontent.com is a legitimate domain name for most antivirus software and host intrusion prevention systems. Its use as a load download address can effectively avoid interception, but it also increases the risk of hacking identity exposure.
Figure 2 Commands executed after hacking the server
Use "Image Steganography" to Hide Malicious Code
The main function of the first stage load content is to download the embedded malicious code image from hxxps://raw.githubusercontent.com/Tree1985/metasploit-framework/master/web.png and obtain the malicious code execution from the image. Web.png is a special image. Hackers use the Invoke-PSImage tool to insert malicious code into it. Invoke-PSImage is a PowerShell image steganography tool developed by Barrett Adams, a foreign security researcher. It can insert malicious code into the last 4 bits of the two color channels G and B in each pixel of the image. Figure 3 shows the simple working principle of Invoke-PSImage.
Invoke-PSImage takes a PowerShell script and embeds the bytes of the script into the pixels of a PNG image. It generates a oneliner for executing either from a file of from the web (when the -Web flag is passed)
Figure 3 The simple working principle of Invoke-PSImage
Since the last 4 bits of the color channel do not have much effect on the color rendering of the final pixel, the picture embedded in the malicious code through Invoke-PSImage is almost the same as the original picture. Hackers' hosting of such a "normal" image on Gist will not raise doubts.
Encrypt important files in your computer and ask for ransom
The second stage of the load is the execution of the encrypted file and ransomware. The payload is also written in PowerShell language.
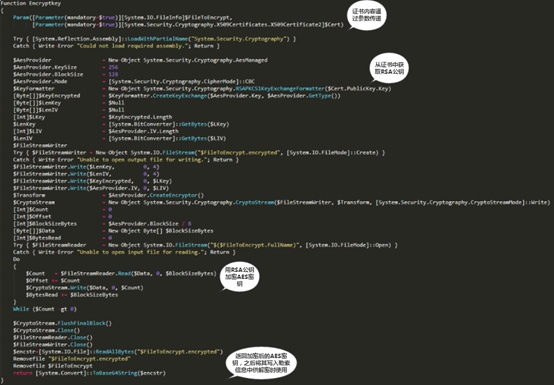
For each computer, the Greystars ransomware virus generates an AES key for encrypting the file and encrypts the AES key with the built-in RSA public key. The RSA public key is stored in a certificate that is hardcoded into the code and is obtained through the PublicKey method of the .NET X509Certificates class. Because the PowerShell language has the flexibility to manipulate .NET methods, Greystars ransomware exploits this feature to make cumbersome key generation and key cryptography use a neat PowerShell language. Figure 4 shows the RSA encryption of AES keys by the Greystars ransomware virus.

Figure 4: RSA encryption of AES keys by Greystars ransomware virus
Greystars ransomware encrypt computer with 422 kinds of file formats, including not only common documents, pictures, database files, but also includes some of the script files required for the server to run, including python scripts, PHP scripts, PowerShell scripts. During the encryption process, the Greystars ransomware virus will avoid other directories except the desktop folder and the document folder in the C drive to ensure the normal operation of the system and end the database-related processes to ensure that the database file is successfully encrypted. Because the Greystars ransomware uses the method of “encrypting the original file à generating a new file ànd deleting the original file”, some directories with only read-only privileges will appear to have the encrypted files that do not exist but the original files are deleted. This results in some The server could not recover the file by paying the ransom. Figure 5 shows the file format encrypted by the Greystars ransomware virus.

All encrypted files will be suffixed with "greystars@protonmail.com". The generated ransom information requires the victim to transfer a ransom of 0.08 bitcoins to the specified address to decrypt the file. Figure 6 shows ransom information.

Figure 6 Help file information
Weblogic and Websphere server began to be favored by ransomware
In 2017, Weblogic broke two serious de-serialization flaws CVE-2017-3248 and CVE-2017-10271, affecting Oracle WebLogic Server 10.3.6.0.0, 12.1.3.0.0, 12.2.1.0, 12.2.1.1, etc. Multiple versions, these two vulnerabilities are also widely used to implant mining Trojans into the server. To date, there are still many servers that have not updated WebLogic.
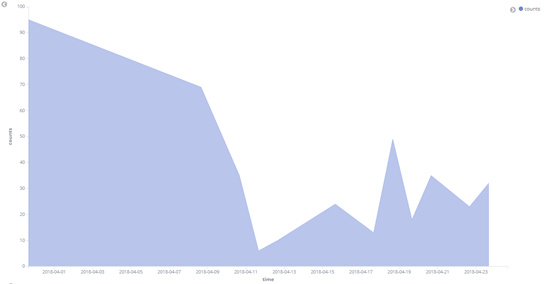
In April 2018, AV monitored two ransomware family Satan and Greystars to attack the Weblogic server. As shown in the trend of Satan ransomware transmission in Figure 7, Satan ransomware has remained active and has affected over a hundred enterprise servers in the country. While the Greystars ransomware virus only broke out on April 21st, it still affected nearly 100 corporate servers.

Figure 7 Trend of the spread of Satan ransom in April
Why the Weblogic server began to be favored by the blackmail virus. There are two main reasons: First, there are a large number of Weblogic servers that are not updated, and vulnerability exploitation attacks are less difficult. For attackers, the ratio of attack revenue to attack costs is very high. Second, such server systems are generally owned by enterprises. The possibility of companies paying ransoms to recover documents is much higher than that of users. Such attacked servers are generally a type of machine that is left unattended or neglected. Attacks on such servers by mining Trojan horses cannot cause too much movement to attract the attention of server administrators and corresponding enterprises, and extortion of viruses. Attacks can cause servers to crash into business operations, which is why blackmail viruses are often exposed.
Protection advice
1. Update the Weblogic server and websphere to the latest version in time.
2. Install security software to intercept such viruses.
Mitigation Actions:
Restrict PSEXEC , wmi access to the servers if they are windows.
Enforce Software Restriction Policies to ensure ransomware protection.
Import the rules that are listed below.
- Path:
%AppData%\*.exe - Security Level:
Disallowed - Description:
Don’t allow executables to run from %AppData%.
- Path if using Windows XP:
%UserProfile%\Local Settings\*.exe - Path if using Windows Vista/7/8:
%LocalAppData%\*.exe
- Security Level:
Disallowed - Description:
Don’t allow executables to run from %AppData%.
- Path:
%AppData%\*\*.exe - Security Level:
Disallowed - Description:
Don’t allow executables to run from immediate subfolders of %AppData%.
- Path if using Windows XP:
%UserProfile%\Local Settings\*\*.exe - Path if using Windows Vista/7/8:
%LocalAppData%\*\*.exe - Security Level:
Disallowed - Description:
Don’t allow executables to run from immediate subfolders of %AppData%.
- Path if using Windows XP:
%UserProfile%\Local Settings\Temp\Rar*\*.exe - Path if using Windows Vista/7/8:
%LocalAppData%\Temp\Rar*\*.exe - Security Level:
Disallowed - Description:
Block executables run from archive attachments opened with WinRAR.
- Path if using Windows XP:
%UserProfile%\Local Settings\Temp\7z*\*.exe - Path if using Windows Vista/7/8:
%LocalAppData%\Temp\7z*\*.exe - Security Level:
Disallowed - Description:
Block executables run from archive attachments opened with 7zip.
- Path if using Windows XP:
%UserProfile%\Local Settings\Temp\wz*\*.exe - Path if using Windows Vista/7/8:
%LocalAppData%\Temp\wz*\*.exe - Security Level:
Disallowed - Description:
Block executables run from archive attachments opened with WinZip.
- Path if using Windows XP:
%UserProfile%\Local Settings\Temp\*.zip\*.exe - Path if using Windows Vista/7/8:
%LocalAppData%\Temp\*.zip\*.exe - Security Level:
Disallowed - Description:
Block executables run from archive attachments opened using Windows built-in Zip support.
Update your websphere 7 with latest Fix Pack 43 (7.0.0.43)
WebSphere Application Server traditional V9.0 Fix Pack 9.0.0.7
WebSphere Application Server traditional V8.5 Fix Pack 8.5.5.13


