A week ago story about state-sponsored Chinese
cyberspies breaking into Fortune 500 companies to steal intellectual
property, personal data and other invaluable assets. Now, researchers
say they’ve unearthed evidence that some of the same Chinese hackers
also have been selling access to compromised computers within those
companies to help perpetuate future breaches.
The so-called “Great Firewall of China” is an effort by the Chinese
government to block citizens from accessing specific content and Web
sites that the government has deemed objectionable. Consequently, many
Chinese seek to evade such censorship by turning to virtual private
network or “VPN” services that allow users to tunnel their Internet
connections to locations beyond the control of the Great Firewall.
Security experts at RSA Research say they’ve identified an archipelago of Chinese-language virtual private network (VPN) services marketed to Chinese online gamers and those wishing to evade censorship, but which also appear to be used as an active platform for launching attacks on non-Chinese corporations while obscuring the origins of the attackers.
Dubbed by RSA as “Terracotta VPN” (a reference to the Chinese Terracotta Army), this satellite array of VPN services “may represent the first exposure of a PRC-based VPN operation that maliciously, efficiently and rapidly enlists vulnerable servers around the world,” the company said in a report released today.
The hacker group thought to be using Terracotta to launch and hide attacks is known by a number of code names, including the “Shell_Crew” and “Deep Panda.” Security experts have tied this Chinese espionage gang to some of the largest data breaches in U.S. history, including the recent attack on the U.S. Office of Personnel Management, as well as the breaches at U.S. healthcare insurers Anthem and Premera.
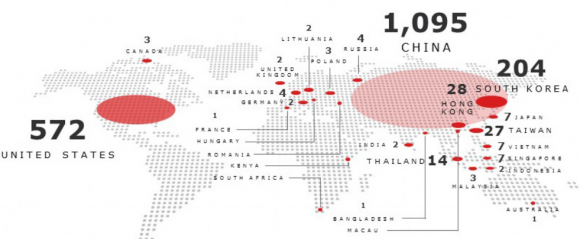
According to RSA, Terracotta VPN has more than 1,500 nodes around the world where users can pop up on the Internet. Many of those locations appear to be little more than servers at Internet service providers in the United States, Korea, Japan and elsewhere that offer cheap virtual private servers.
But RSA researchers said they discovered that many of Terracotta’s exit nodes were compromised Windows servers that were “harvested” without the victims’ knowledge or permission, including systems at a Fortune 500 hotel chain; a hi-tech manufacturer; a law firm; a doctor’s office; and a county government of a U.S. state.
The report steps through a forensics analysis that RSA conducted on one of the compromised VPN systems, tracking each step the intruders took to break into the server and ultimately enlist the system as part of the Terracotta VPN network.
“All of the compromised systems, confirmed through victim-communication by RSA Research, are Windows servers,” the company wrote. “RSA Research suspects that Terracotta is targeting vulnerable Windows servers because this platform includes VPN services that can be configured quickly (in a matter of seconds).”
RSA says suspected nation-state actors have leveraged at least 52 Terracotta VPN nodes to exploit sensitive targets among Western government and commercial organizations. The company said it received a specific report from a large defense contractor concerning 27 different Terracotta VPN node Internet addresses that were used to send phishing emails targeting users in their organization.
“Out of the thirteen different IP addresses used during this campaign against this one (APT) target, eleven (85%) were associated with Terracotta VPN nodes,” RSA wrote of one cyber espionage campaign it investigated. “Perhaps one of the benefits of using Terracotta for Advanced Threat Actors is that their espionage related network traffic can blend-in with ‘otherwise-legitimate’ VPN traffic.”
DIGGING DEEPER
RSA’s report includes a single screen shot of software used by one of the commercial VPN services marketed on Chinese sites and tied to the Terracotta network, but for me this was just a tease: I wanted a closer look at this network, yet RSA (or more likely, the company’s lawyers) carefully omitted any information in its report that would make it easy to locate the sites selling or offering the Terracotta VPN.
RSA said the Web sites advertising the VPN services are marketed on Chinese-language Web sites that are for the most part linked by common domain name registrant email addresses and are often hosted on the same infrastructure with the same basic Web content. Along those lines, the company did include one very useful tidbit in its report: A section designed to help companies detect servers that may be compromised warned that any Web servers seen phoning home to 8800free[dot]info should be considered hacked.
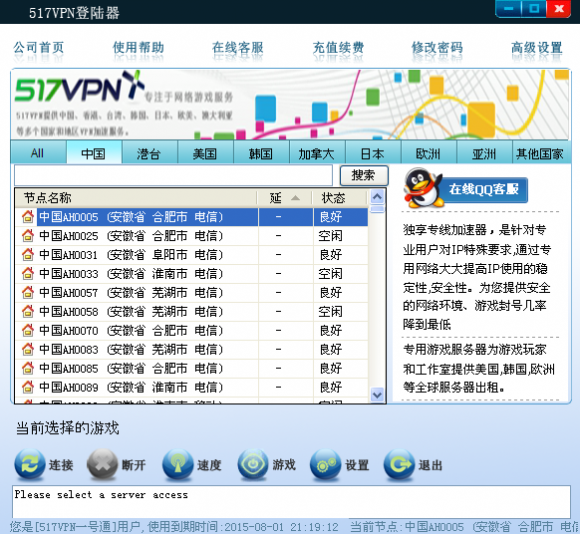
Armed with lists of dozens of VPN sites, it wasn’t hard to find several sites offering different VPN clients for download. I installed each on a carefully isolated virtual machine (don’t try this at home, kids!). Here’s one of those sites:
All told, I managed to download, install and use at least three VPN
clients from VPN service domains tied to the above-mentioned email
addresses. The Chinese-language clients were remarkably similar in
overall appearance and function, and listed exit nodes via tabs for
several countries, including the Canada, Japan, South Korea and the
United States, among others.
RSA said it found more than 500 Terracotta servers that were U.S. based, they have gotten in on the fun after the company started notifying victim organizations because they found only a few dozen U.S.-based hosts in any of the VPN clients they checked. And most of the ones they did find that were based in the United States appeared to be virtual private servers at a handful of hosting companies.
The one exception they found was a VPN node tied to a dedicated Windows server for the Web site of a company in Michigan that manufactures custom-made chairs for offices, lounges and meeting rooms. Contacted by them , the company confirmed that its server was infected and beaconing home to the control servers described in the RSA report.
In addition to the U.S.-based hosts, they managed to step through a huge number of systems based in South Korea. They didn’t have time to look through each record to see whether any of the Korean exit nodes were interesting.
Assuming RSA’s research is accurate the idea of hackers selling access to hacked PCs for anonymity and stealth online is hardly a new one.
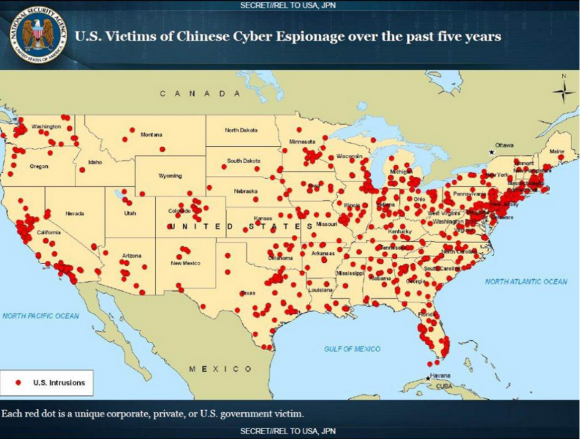
It is, after all, incredibly common for malicious hackers to use systems they’ve hacked to help perpetrate future cybercrimes – particularly espionage attacks. A classified map of the United States obtained by NBC last week showing the victims of Chinese cyber espionage over the past five years lights up like so many exit nodes in a VPN network.

Security experts at RSA Research say they’ve identified an archipelago of Chinese-language virtual private network (VPN) services marketed to Chinese online gamers and those wishing to evade censorship, but which also appear to be used as an active platform for launching attacks on non-Chinese corporations while obscuring the origins of the attackers.
Dubbed by RSA as “Terracotta VPN” (a reference to the Chinese Terracotta Army), this satellite array of VPN services “may represent the first exposure of a PRC-based VPN operation that maliciously, efficiently and rapidly enlists vulnerable servers around the world,” the company said in a report released today.
The hacker group thought to be using Terracotta to launch and hide attacks is known by a number of code names, including the “Shell_Crew” and “Deep Panda.” Security experts have tied this Chinese espionage gang to some of the largest data breaches in U.S. history, including the recent attack on the U.S. Office of Personnel Management, as well as the breaches at U.S. healthcare insurers Anthem and Premera.
According to RSA, Terracotta VPN has more than 1,500 nodes around the world where users can pop up on the Internet. Many of those locations appear to be little more than servers at Internet service providers in the United States, Korea, Japan and elsewhere that offer cheap virtual private servers.
But RSA researchers said they discovered that many of Terracotta’s exit nodes were compromised Windows servers that were “harvested” without the victims’ knowledge or permission, including systems at a Fortune 500 hotel chain; a hi-tech manufacturer; a law firm; a doctor’s office; and a county government of a U.S. state.
The report steps through a forensics analysis that RSA conducted on one of the compromised VPN systems, tracking each step the intruders took to break into the server and ultimately enlist the system as part of the Terracotta VPN network.
“All of the compromised systems, confirmed through victim-communication by RSA Research, are Windows servers,” the company wrote. “RSA Research suspects that Terracotta is targeting vulnerable Windows servers because this platform includes VPN services that can be configured quickly (in a matter of seconds).”
RSA says suspected nation-state actors have leveraged at least 52 Terracotta VPN nodes to exploit sensitive targets among Western government and commercial organizations. The company said it received a specific report from a large defense contractor concerning 27 different Terracotta VPN node Internet addresses that were used to send phishing emails targeting users in their organization.
“Out of the thirteen different IP addresses used during this campaign against this one (APT) target, eleven (85%) were associated with Terracotta VPN nodes,” RSA wrote of one cyber espionage campaign it investigated. “Perhaps one of the benefits of using Terracotta for Advanced Threat Actors is that their espionage related network traffic can blend-in with ‘otherwise-legitimate’ VPN traffic.”
DIGGING DEEPER
RSA’s report includes a single screen shot of software used by one of the commercial VPN services marketed on Chinese sites and tied to the Terracotta network, but for me this was just a tease: I wanted a closer look at this network, yet RSA (or more likely, the company’s lawyers) carefully omitted any information in its report that would make it easy to locate the sites selling or offering the Terracotta VPN.
RSA said the Web sites advertising the VPN services are marketed on Chinese-language Web sites that are for the most part linked by common domain name registrant email addresses and are often hosted on the same infrastructure with the same basic Web content. Along those lines, the company did include one very useful tidbit in its report: A section designed to help companies detect servers that may be compromised warned that any Web servers seen phoning home to 8800free[dot]info should be considered hacked.
Armed with lists of dozens of VPN sites, it wasn’t hard to find several sites offering different VPN clients for download. I installed each on a carefully isolated virtual machine (don’t try this at home, kids!). Here’s one of those sites:
A Google-translated version of one of the sites offering the VPN software and service that RSA has dubbed “Terracotta.”

RSA said it found more than 500 Terracotta servers that were U.S. based, they have gotten in on the fun after the company started notifying victim organizations because they found only a few dozen U.S.-based hosts in any of the VPN clients they checked. And most of the ones they did find that were based in the United States appeared to be virtual private servers at a handful of hosting companies.
The one exception they found was a VPN node tied to a dedicated Windows server for the Web site of a company in Michigan that manufactures custom-made chairs for offices, lounges and meeting rooms. Contacted by them , the company confirmed that its server was infected and beaconing home to the control servers described in the RSA report.
In addition to the U.S.-based hosts, they managed to step through a huge number of systems based in South Korea. They didn’t have time to look through each record to see whether any of the Korean exit nodes were interesting.
Assuming RSA’s research is accurate the idea of hackers selling access to hacked PCs for anonymity and stealth online is hardly a new one.
It is, after all, incredibly common for malicious hackers to use systems they’ve hacked to help perpetrate future cybercrimes – particularly espionage attacks. A classified map of the United States obtained by NBC last week showing the victims of Chinese cyber espionage over the past five years lights up like so many exit nodes in a VPN network.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.