One came with this story about a practical application of big data
analysis as applied to the trove of sensor readings taken by satellites
and by ground-based senosrs. A company called Terra Seismic says that
earthquakes can be predicted 20-30 days before they occur,
by sifting data for thermal, ionic, and other abnormalities in areas
where quakes are considered likely. Says the linked article: "The
company claims to have successfully predicted a number of earthquakes.
For example, on 5th of April 2013, the firm issued a forecast for Japan.
On 12th April 2013, an earthquake hit the identified area and 33 people
were injured. On 4th June 2013, the firm again made a prediction for an
earthquake in North Italy. On 21st June, an earthquake hit the
identified area. On 3rd March 2013, the firm issued a forecast for an
earthquake in Iran. Again, after 35 days, an earthquake hit the
identified area."
Tuesday, May 12, 2015
Prison Messaging System JPay Withdraws Copyright Claims
Florida-based JPay has a specialized business model and an audience that
is at least in part a (literally) captive one: the company specializes
in logistics and communications services involving prisons and
prisoners, ranging from payment services to logistics to electronic
communications with prisoners. Now, via Cory Doctorow at Boing Boing comes a report from the EFF that the company has back-pedaled
on a particularly strange aspect of the terms under which the company
provided messaging services for prisoners: namely, JPay's terms of
service made exhaustive copyright claims on messages sent by prisoners,
claiming rights to "all content, whether it be text, images, or video"
send via the service. That language has now been excised, but not in
time to prevent at least one bad outcome; from the EFF's description:
[Valerie] Buford has been running a social media campaign to overturn
her [brother, Leon Benson's] murder conviction. However, after Buford
published a videogram that her brother recorded via JPay to Facebook,
prison administrators cut off her access to the JPay system, sent Benson
to solitary confinement, and stripped away some of his earned "good
time." To justify the discipline, prison officials said they were
enforcing JPay's intellectual property rights and terms of service.
Photobucket Hackers Nabbed, Face Serious Charges From US Authorities
The U.S. Department of Justice said in a statement released Friday that two men, Brandon Bourret, and Athanasios Andrianakis, of Colorado Springs, Colorado
and Sunnyvale, California, respectively, were arrested
for their sale of software designed to breach the security of
photo-sharing site Photobucket.com; their "Photofucket" app, says the
linked Register report, was used "to plunder Photobucket's users'
private and password-protected information, images and videos, it has
been alleged ... The charge sheet against Bourret and Andrianakis
details one count of conspiracy and one count of computer fraud, aid and
abet – both of which carry a maximum prison sentence of five years and a
fine of up to $250,000.
In addition, the men stand accused of two counts of access device fraud,
which carries a higher prison sentence of up to 10 years and a fine of
up to a quarter of a million dollars, per count." The indictment, filed in Federal District Court in Colorado, is far easier to read than many.
Monday, May 11, 2015
Anonymous Tor Cloud Project Closes Down
The Tor browser is used by many to stay anonymous online — and it's
something that has been embraced by the likes of WikiLeaks as a way to
safely gather information whilst hopefully avoiding the surveillance of
the NSA. One lesser known project from the same stables is the Tor Cloud
service, and Tor has announced that it is closing down.
Based on the Amazon EC2 cloud computing platform, Tor Cloud provided a way to share computing resources and allow faster uncensored access to the internet. However, the project is plagued with 'at least one major bug ... that makes it completely dysfunctional' and after failing to find anyone to undertake the work, the decision was taken to shutter Tor Cloud. This does not mean that Tor itself is dead — far from it — and developers are being encouraged to create their own forked versions of Tor Cloud.
Based on the Amazon EC2 cloud computing platform, Tor Cloud provided a way to share computing resources and allow faster uncensored access to the internet. However, the project is plagued with 'at least one major bug ... that makes it completely dysfunctional' and after failing to find anyone to undertake the work, the decision was taken to shutter Tor Cloud. This does not mean that Tor itself is dead — far from it — and developers are being encouraged to create their own forked versions of Tor Cloud.
Uber Wants To Buy Nokia's Mapping Services
When Nokia sold its handset business to Microsoft, one of the
services left that it intended to rebuild the company on was Here, its
rival to Google Maps. But now a deal is said to be in the works to sell Here to Uber,
a company that relies heavily on navigation services and that doesn't
want to end up too reliant on Google, a potential rival in the
futuristic self-driving car business.
Sunday, May 10, 2015
Via PayPal Your Online Accounts are being sold
Normally, if one wishes to buy stolen account credentials for paid online services like Netflix, Hulu, XBox Live or Spotify, the buyer needs to visit a cybercrime forum or drop into a dark Web marketplace that only accepts Bitcoin as payment. Increasingly, however, these accounts are showing up for sale at Payivy[dot]com, an open Web marketplace that happily accepts PayPal in exchange for a variety of stolen accounts.
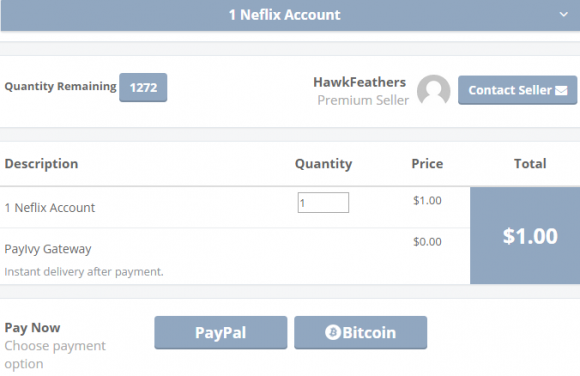 Marketed and sold by a Hackforums user named “Sh1eld” as a supposed method of selling ebooks and collecting payments for affiliate marketers, PayIvy has instead become a major conduit for hawking stolen accounts and credentials for a range of top Web services.
Marketed and sold by a Hackforums user named “Sh1eld” as a supposed method of selling ebooks and collecting payments for affiliate marketers, PayIvy has instead become a major conduit for hawking stolen accounts and credentials for a range of top Web services.
There is no central index of items for sale via PayIvy per se, but this catalog of cached sales threads offers a fairly representative glimpse: License keys for Adobe and Microsoft software products, user account credentials in bulk for services like Hulu, Netflix, Spotify, DirecTV and HBO Go, as well as a raft of gaming accounts at Origin, Steam, PlayStation and XBox Live. Other indexes at archive.is and PayIvy’s page at Reddit reveal similar results.
It’s not clear how or why PayPal isn’t shutting down most of these merchants, but some of the sellers clearly are testing things to see how far they can push it: In just five minutes of searching online, I found several PayIvy sellers who were accepting PayPal payments via PayIvy for…wait for it…hijacked PayPal accounts! The fact that PayIvy takes PayPal as payment means that buyers can purchase hacked accounts with [stolen] credit cards — or, worse yet, stolen PayPal accounts.
Jack Christin, Jr., associate general counsel at PayPal, said while the site itself is not in violation of its Acceptable Use Policies (AUP), there have been cases where PayPal has identified accounts selling goods that violate its policy and in those cases, the company has have exited those merchants from its system.
“PayPal proactively monitors sellers with PayPal accounts who use the Paylvy platform to ensure the products they are selling are in compliance with our AUP, and we take appropriate action when violations are discovered,” Christin said.
The proprietor of PayIvy (quite possibly this guy, according to many of his fellow Hackforums users) makes money off of the service by selling “premium” accounts, which apparently offer repeat sellers a way to better track and manage their sales. Appropriately enough, among his ebook offerings via PayIvy is a tutorial on how to avoid getting one’s account banned or limited by PayPal. PayIvy did not respond to requests for comment.
Sh1eld makes clear how he feels about his users selling hacked accounts to pay services via his site in this thread, where he posts about takedown requests from a company representing Netflix.
“We are not under any obligation to follow any site’s TOS [terms of service],” he wrote. “However, we will take actions regarding copyrighted content, malicious files, or child pornography.”
I wonder how this individual would feel about people selling stolen PayIvy premium accounts?
If you’re curious about the underground’s interest in and valuation of your online accounts, take a look at my primers on this subject, including The Value of a Hacked Email Account and the Value of a Hacked PC. Want pointers on how to avoid becoming the next victim?

A
PayIvy seller advertising Netflix accounts for a dollar apiece. Unlike
most sites selling hacked accounts, this one takes PayPal.
There is no central index of items for sale via PayIvy per se, but this catalog of cached sales threads offers a fairly representative glimpse: License keys for Adobe and Microsoft software products, user account credentials in bulk for services like Hulu, Netflix, Spotify, DirecTV and HBO Go, as well as a raft of gaming accounts at Origin, Steam, PlayStation and XBox Live. Other indexes at archive.is and PayIvy’s page at Reddit reveal similar results.
It’s not clear how or why PayPal isn’t shutting down most of these merchants, but some of the sellers clearly are testing things to see how far they can push it: In just five minutes of searching online, I found several PayIvy sellers who were accepting PayPal payments via PayIvy for…wait for it…hijacked PayPal accounts! The fact that PayIvy takes PayPal as payment means that buyers can purchase hacked accounts with [stolen] credit cards — or, worse yet, stolen PayPal accounts.
Jack Christin, Jr., associate general counsel at PayPal, said while the site itself is not in violation of its Acceptable Use Policies (AUP), there have been cases where PayPal has identified accounts selling goods that violate its policy and in those cases, the company has have exited those merchants from its system.
“PayPal proactively monitors sellers with PayPal accounts who use the Paylvy platform to ensure the products they are selling are in compliance with our AUP, and we take appropriate action when violations are discovered,” Christin said.
The proprietor of PayIvy (quite possibly this guy, according to many of his fellow Hackforums users) makes money off of the service by selling “premium” accounts, which apparently offer repeat sellers a way to better track and manage their sales. Appropriately enough, among his ebook offerings via PayIvy is a tutorial on how to avoid getting one’s account banned or limited by PayPal. PayIvy did not respond to requests for comment.
Sh1eld makes clear how he feels about his users selling hacked accounts to pay services via his site in this thread, where he posts about takedown requests from a company representing Netflix.
“We are not under any obligation to follow any site’s TOS [terms of service],” he wrote. “However, we will take actions regarding copyrighted content, malicious files, or child pornography.”
I wonder how this individual would feel about people selling stolen PayIvy premium accounts?
If you’re curious about the underground’s interest in and valuation of your online accounts, take a look at my primers on this subject, including The Value of a Hacked Email Account and the Value of a Hacked PC. Want pointers on how to avoid becoming the next victim?
Cybersecurity Company Extorted Its Clients, Says Whistleblower
Richard
Wallace used to be an investigator for Tiversa, a cybersecurity company
that sells services like "breach protection" and "incident response."
These days, Wallace is testifying in federal court that Tiversa faked breaches to encourage sales, and extorted clients that weren't interested.
For example, Wallace said Tiversa targeted a cancer testing center
called LabMD in 2010, tapping into their computers and downloading
medical records. Tiversa then used those records as evidence to convince
LabMD they had been hacked, offering its "incident response" service at
the same time. LabMD didn't fall for it, so Tiversa told the FTC about
the "hack." The FTC, none-the-wiser, went after LabMD in court,
eventually destroying the business. Wallace has also cast suspicion on
reports Tiversa has issued, including one saying President Obama's
helicopter blueprints were found on Iranian computers.
Subscribe to:
Posts (Atom)